
Here i want to share about my write-up for the room n8n: CVE-2025-68613 ↗, Learn how adversaries can exploit the CVE-2025-68613 vulnerability in n8n. Hope it is useful for learning about cybersecurity.
Task 1: Introduction#
CVE-2025-68613 is a critical vulnerability (CVSS 9.9) in the n8n workflow automation platform, published in December 2025. This vulnerability is a Remote Code Execution (RCE) flaw found in the workflow expression evaluation system, affecting versions 0.211.0 through 1.120.3. It allows authenticated attackers to execute system-level commands by injecting malicious JavaScript code. Users are strongly advised to update to patched versions (1.120.4, 1.121.1, or 1.122.0) to secure their instances.
Let’s dive into the technical details.
No answer needed
Task 2: Technical Background#
n8n is built on Node.js and uses an Expression Evaluation System to process dynamic user input wrapped in {{ }}. The vulnerability exists because this system lacks proper sandboxing. An attacker can escape the intended context by using this to access the global Node.js object. The exploit chain typically involves accessing this.process.mainModule, loading the child_process module via require(), and finally executing system commands (e.g., execSync('id')). This demonstrates a fundamental breach of security boundaries where user expressions gain access to the underlying runtime environment.
In this exploit, what is the name of the module that allowed us to execute system commands?
child_process
Task 3: Exploitation#
To exploit this vulnerability, an attacker logs into the n8n dashboard (e.g., using tryhackme@thm.local) and creates a new workflow. The method involves adding a “Manual Trigger” connected to an “Edit Fields (Set)” node. Inside the “Edit Fields” node, the attacker adds a new field and pastes the malicious JavaScript payload (containing the sandbox escape code) into the value field. Upon clicking “Execute step,” the code runs on the server, and the output of the system command (such as the id command) is displayed in the interface.
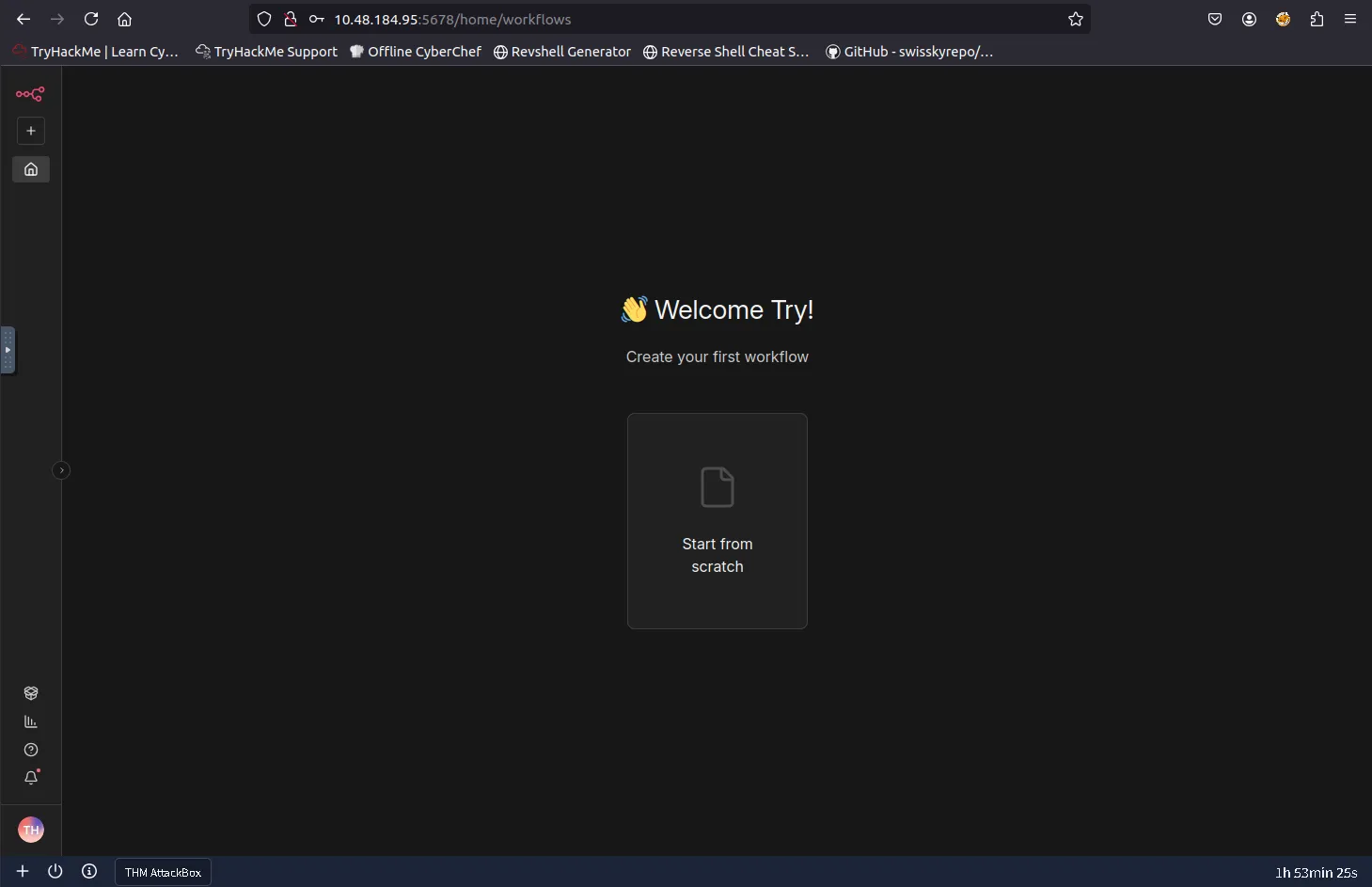
Landing page after logging into the n8n dashboard.
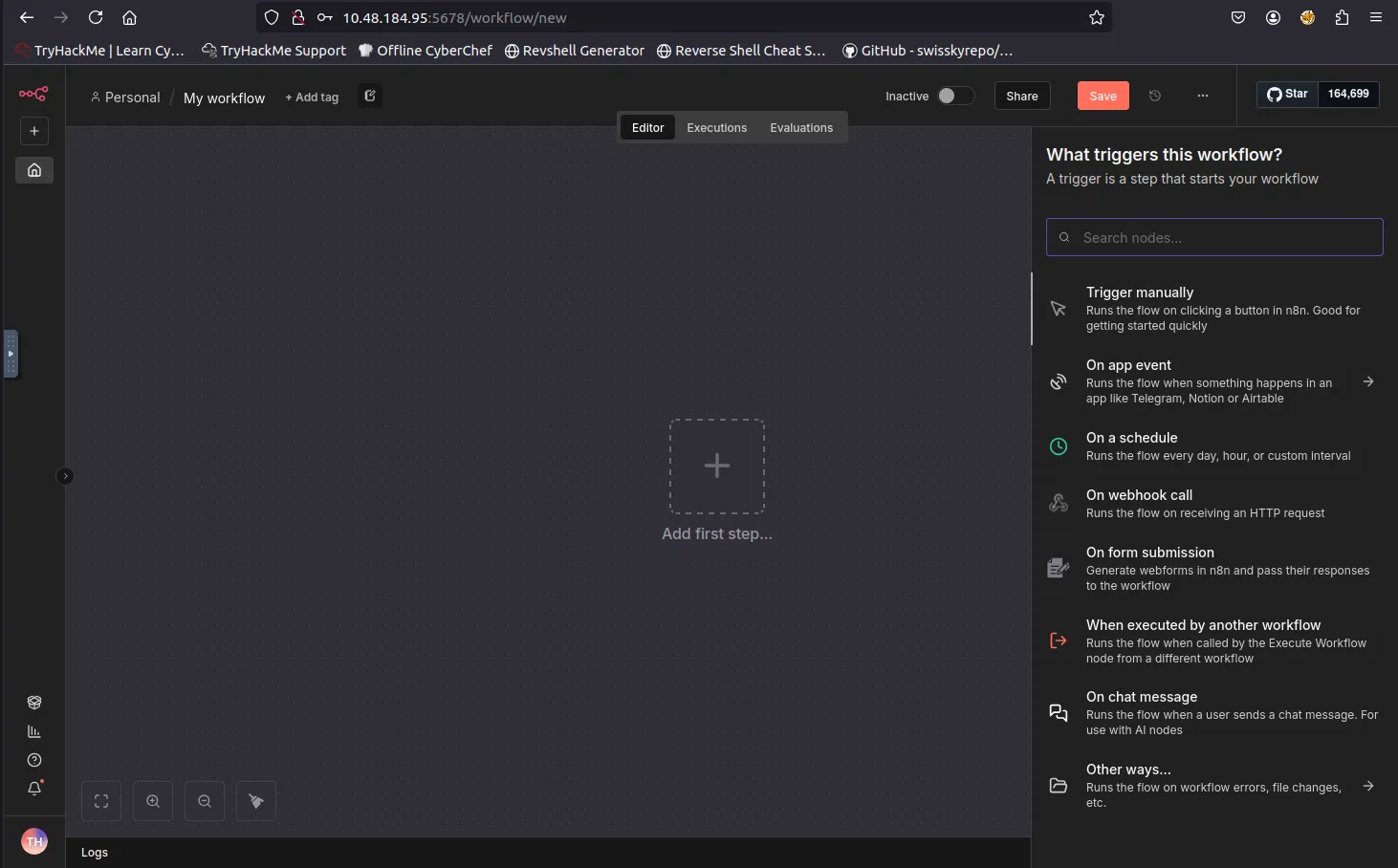
Creating a new workflow by selecting Start from scratch.
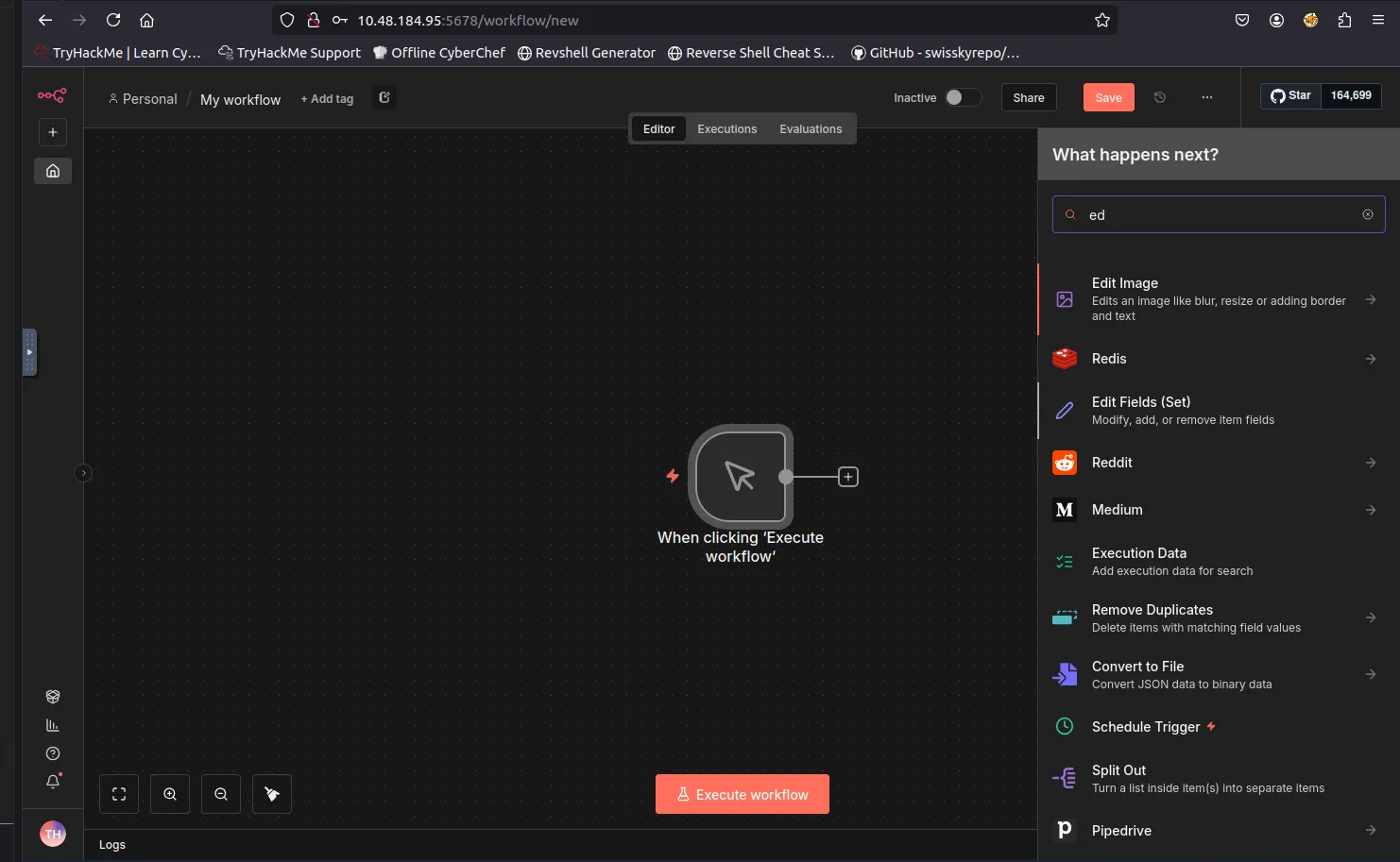
Choosing Manual Trigger as the first workflow step.
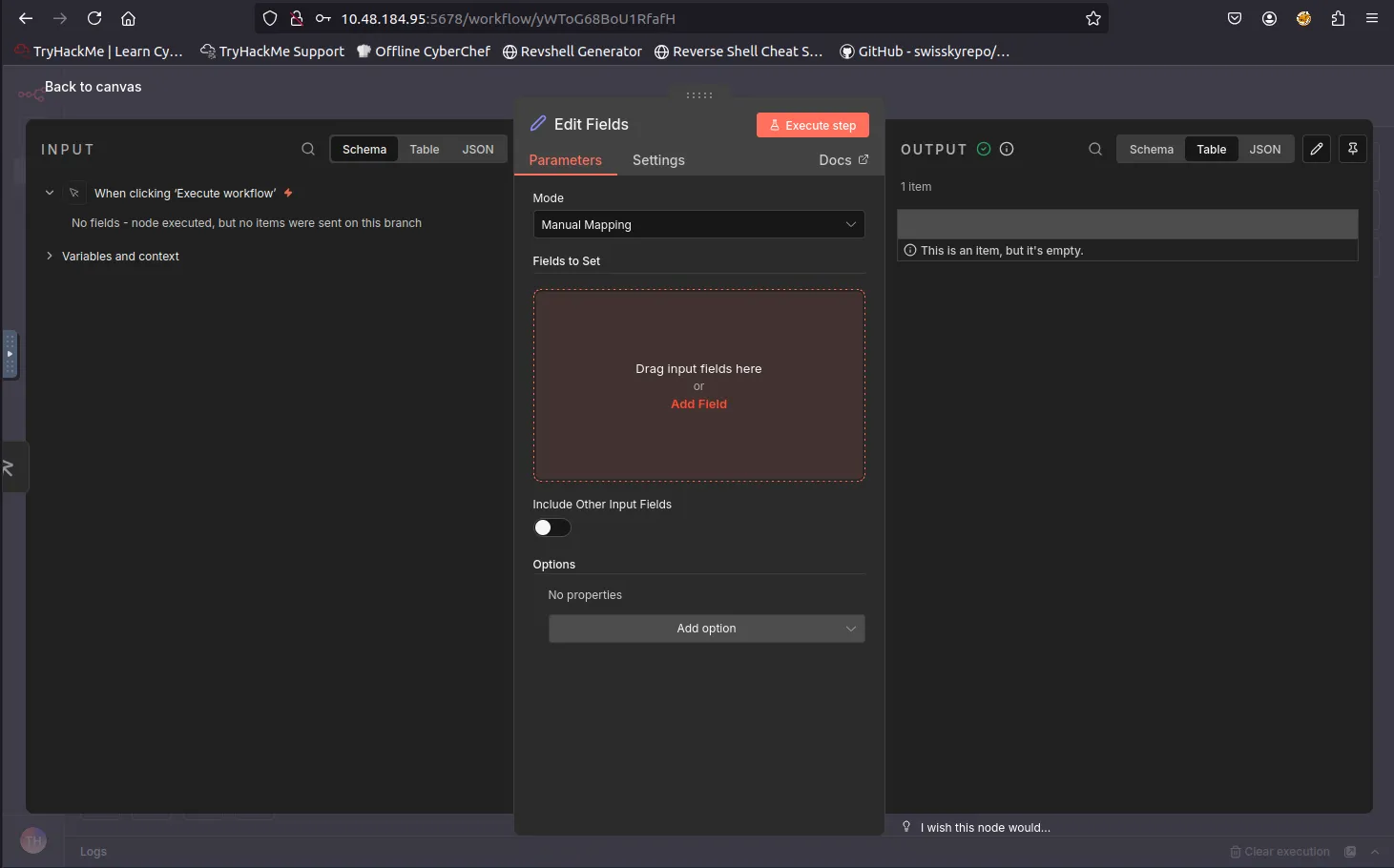
Adding the Edit Fields (Set) node to the workflow.
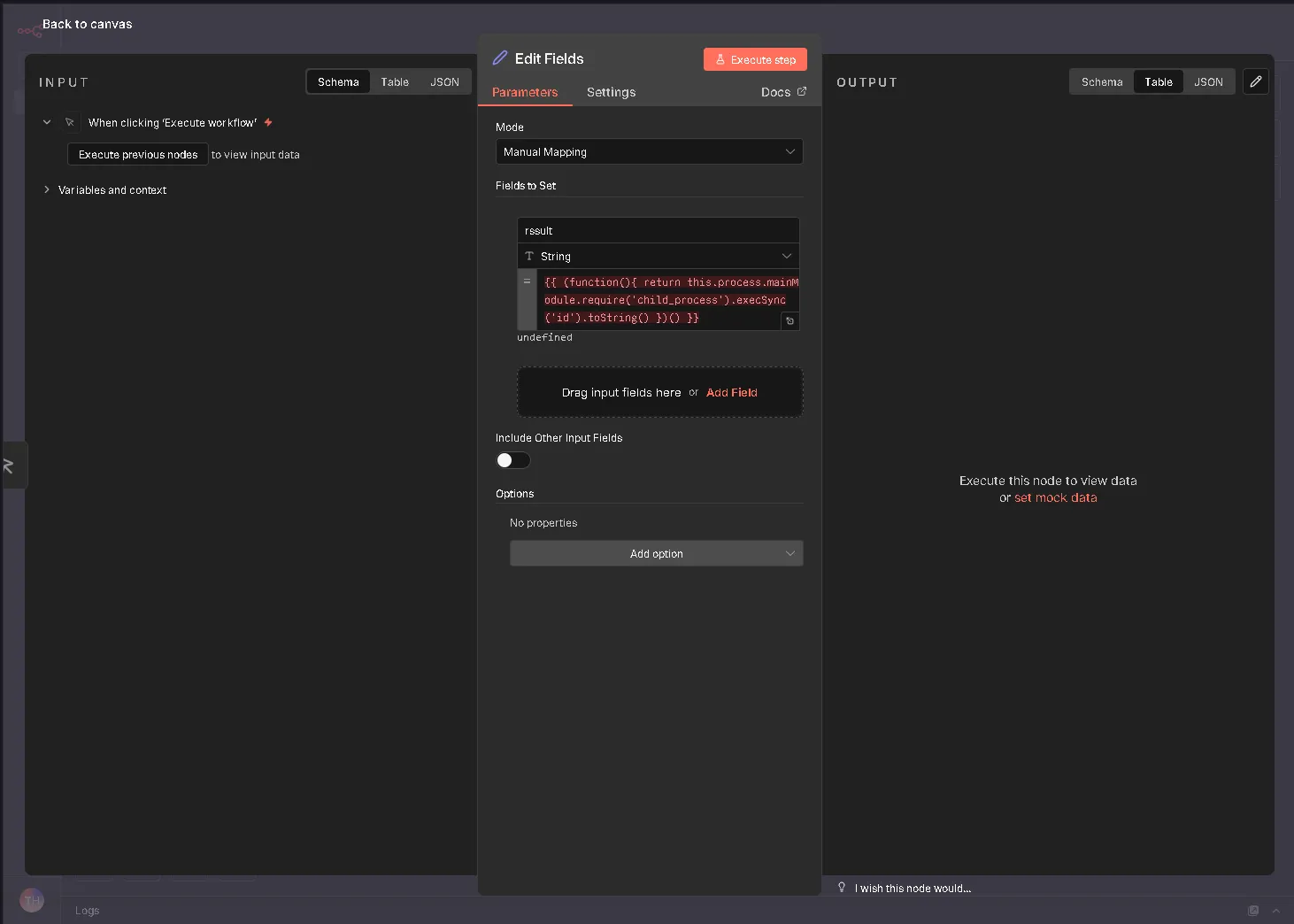
Injecting the malicious JavaScript expression into a new field.
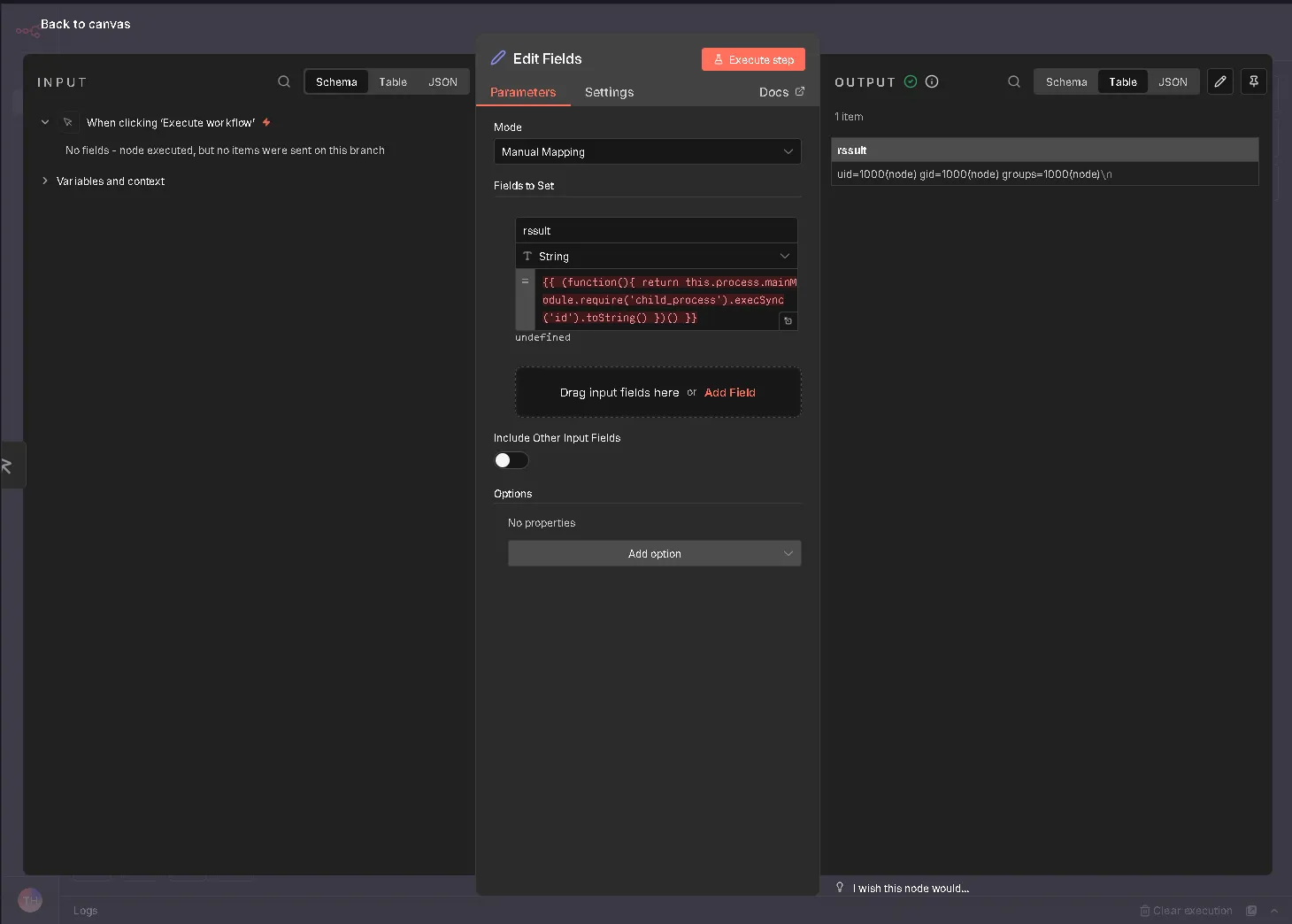
Executing the workflow step to trigger server-side command execution.
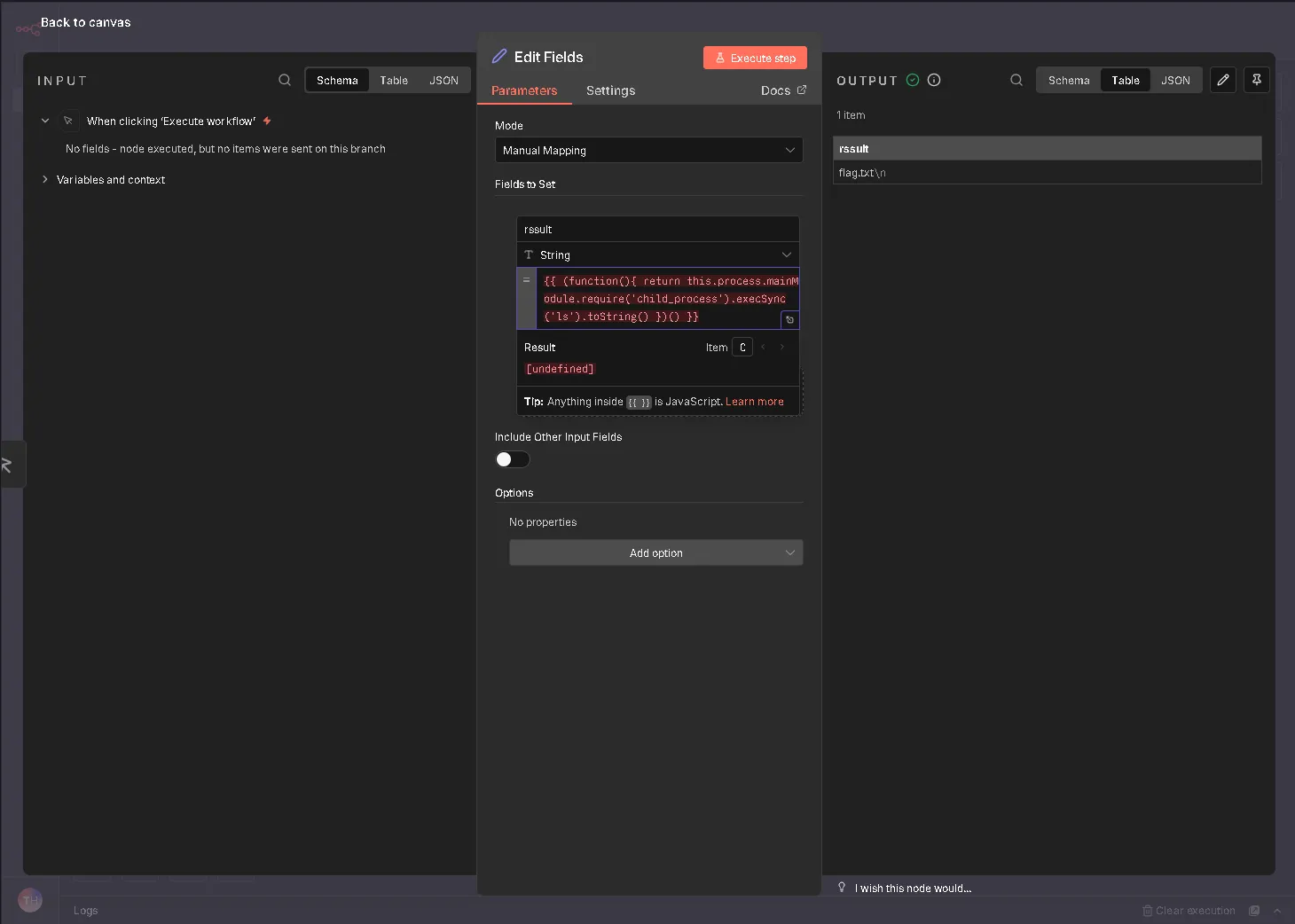
Successful execution of the id command, confirming RCE.
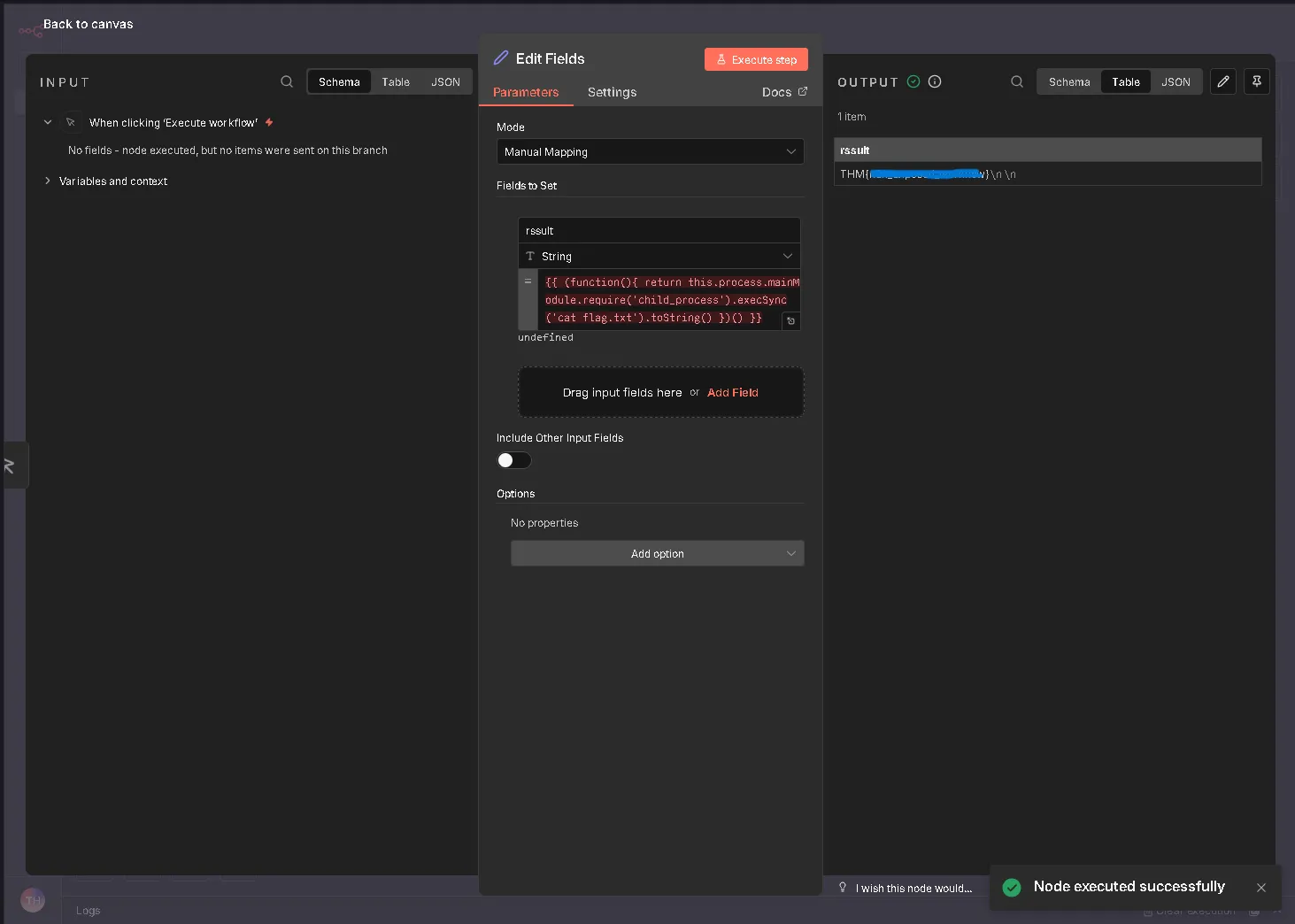
Reading the flag file (flag.txt) directly from the server.
What is the flag?
THM()
Task 4: Detection#
Since n8n’s native logging is limited, detection is best achieved by using a proxy (like Nginx) to log web request bodies. Security teams can use Sigma rules to scan these logs for specific patterns in POST requests to /rest/workflows, looking for keywords like this.process.mainModule, execSync, and child_process. Additionally, it is critical to monitor the operating system for suspicious process creation events—such as reverse shells or reconnaissance commands—to identify post-exploitation activity.
Depending on your environment, ensure that your security solutions are detecting threats targeting your web applications and infrastructure.
No answer needed
Task 5: Conclusion#
This vulnerability highlights the severe risks associated with insecure expression evaluation and flawed trust boundaries between user input and the application runtime. Understanding this exploit helps in developing better detection strategies that focus on context escalation patterns. The most effective mitigation is to ensure the n8n server is upgraded to a secure, patched version immediately.
If you enjoyed this room, consider checking other rooms in the Recent Threats module.
No answer needed